 Admin 2008 -->
Admin 2008 -->
 Admin 2008 -->
Admin 2008 -->
For some more
general PPP and VPN info, search the page (F3) for IPSEC, VPN, or PPP at:
http://www.6530b/CCNACrib.mht
Setting up a linux pptp server - quick summary
apt-get install pptpd
relevant files:
/etc/ppp/options - no change
Edit /etc/ppp/chap-secrets to suit. A * means from
any IP address
vi /etc/ppp/chap-secrets
# Secrets for authentication using CHAP
# clientserversecret IP addresses
uname pptpd password *
The pptpd
name above relates to the auth setting in /etc/ppp/pptpd -options
# Authentication
# Name of the local system for authentication purposes
# (must match the second field in /etc/ppp/chap-secrets
entries)
name pptpd
The rest of this file defaults are fine.
Change the # (Recommended) section settings to match the local server IP and
VPN client pool to suit in:
vi /etc/pptpd.conf
eg:
# (Recommended)
localip 192.168.0.8
remoteip 192.168.0.200-220
Test the config by creating a VPN in Windows to this
server inside the LAN first to check the Linux server is working:
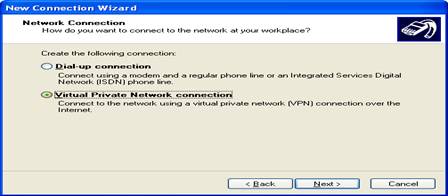
Continue to
wizard end then edit VPN server IP accordingly:
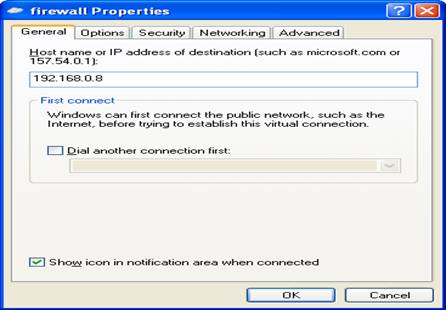
Auto or pptp will do as windows negotiates VPN parameters well
generally (bloody hell! They got something else right!):
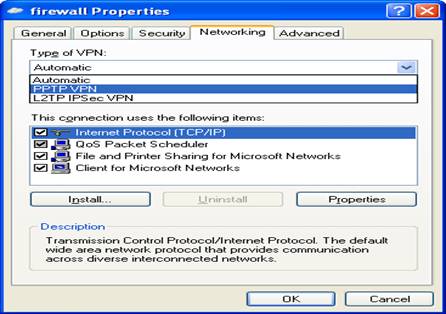
You can monitor
the connection on the server in real time with:
tail -f /var/log/syslog
Start the
connection in windows after adding the password you set in chap-secrets:
tail -f /var/log/syslog
Mar 22 10:18:55
firewall pptpd[3999]: CTRL: Client 192.168.0.2 control connection finished
Mar 22 11:17:01
firewall /USR/SBIN/CRON[14748]: (root) CMD (cd / &&
run-parts --report /etc/cron.hourly)
Mar 22 12:17:01 firewall
/USR/SBIN/CRON[25742]: (root) CMD (cd / &&
run-parts --report /etc/cron.hourly)
Mar 22 13:17:01
firewall /USR/SBIN/CRON[4258]: (root) CMD (cd / &&
run-parts --report /etc/cron.hourly)
Mar 22 13:49:43
firewall pptpd[10191]: CTRL: Client 192.168.0.2 control connection started
Mar 22 13:49:43
firewall pptpd[10191]: CTRL: Starting call (launching pppd,
opening GRE)
Mar 22 13:49:43
firewall pppd[10193]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so
loaded.
Mar 22 13:49:43
firewall pppd[10193]: pppd 2.4.4 started by
root, uid 0
Mar 22 13:49:43
firewall pppd[10193]: Using interface ppp0
Mar 22 13:49:43
firewall pppd[10193]: Connect: ppp0 <--> /dev/pts/0
Mar 22 13:49:43
firewall pptpd[10191]: GRE: Bad checksum from pppd.
Mar 22 13:49:43
firewall pptpd[10191]: CTRL: Ignored a SET LINK INFO packet with real
ACCMs!
Mar 22 13:49:43
firewall pppd[10193]: MPPE 128-bit stateless compression enabled
Mar 22 13:49:45
firewall pppd[10193]: found interface eth0 for proxy arp
Mar 22 13:49:45
firewall pppd[10193]: localIP
address 192.168.0.8
Mar 22 13:49:45
firewall pppd[10193]: remote IP address 192.168.0.200
Note the ppp address allocated from the pool set in /etc/pptpd.conf
# (Recommended)
localip 192.168.0.8
remoteip 192.168.0.200-220
:
ifconfig
eth0
Link encap:EthernetHWaddr
00:20:ed:35:ff:f4
inet
addr:192.168.0.8
Bcast:192.168.0.255
Mask:255.255.255.0
inet6 addr: fe80::220:edff:fe35:fff4/64 Scope:Link
UP BROADCAST RUNNING MULTICASTMTU:1500Metric:1
RX packets:78651
errors:0 dropped:0 overruns:0 frame:0
TX packets:108876
errors:0 dropped:0 overruns:15 carrier:0
collisions:0
txqueuelen:1000
RX bytes:6933271
(6.6 MiB)TX
bytes:33750055 (32.1 MiB)
Interrupt:18
Base address:0xcc00
lo
Link encap:Local Loopback
inet
addr:127.0.0.1Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNINGMTU:16436Metric:1
RX packets:3826
errors:0 dropped:0 overruns:0 frame:0
TX packets:3826
errors:0 dropped:0 overruns:0 carrier:0
collisions:0
txqueuelen:0
RX bytes:819258
(800.0 KiB)TX
bytes:819258 (800.0 KiB)
ppp0
Link encap:Point-to-Point Protocol
inet
addr:192.168.0.8P-t-P:192.168.0.200
Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICASTMTU:1396Metric:1
RX packets:110
errors:0 dropped:0 overruns:0 frame:0
TX packets:179
errors:0 dropped:0 overruns:0 carrier:0
collisions:0
txqueuelen:3
RX bytes:9266
(9.0 KiB)TX
bytes:39314 (38.3 KiB)
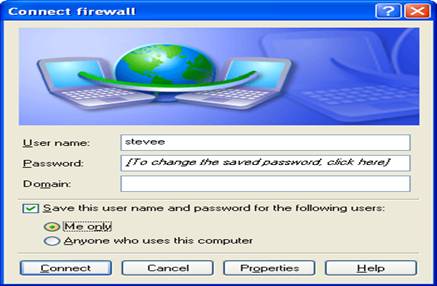
Note the default
route for the win client now changes also to itself and the GW:
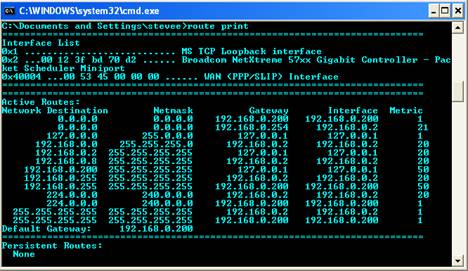
It is added to
the server also:
route
Kernel IP routing
table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.0.200
* 255.255.255.255
UH 0 0 0 ppp0
192.168.0.0 * 255.255.255.0 U
0 0 0 eth0
default
192.168.0.254 0.0.0.0 UG
0 0 0 eth0
VPN and Firewalling with SDM
I manually added:
ip nat inside source static udp
192.168.0.8 1723 interface Dialer0 1723
ip nat inside source static udp
192.168.0.8 500 interface Dialer0 500
ip nat inside source static tcp
192.168.0.8 500 interface Dialer0 500
ip nat inside source static tcp
192.168.0.8 1723 interface Dialer0 1723
but for a working VPN conf with Firewall the missing
line on firewall addition preventing connection was
access-list
101 permit gre any any. The 5900 lines are an attempt to allow VNC
also. The "ip nat source static..." rule is the same format for the VNC port 5901 as for the VPN on 1723, and allowing a "permit ip any any eq 5901" rule in access-list 101 also.
--------------------------------------------------
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname
c837
!
boot-start-marker
boot-end-marker
!
logging buffered alerts
logging console critical
enable secret 5
$1$bKbq$6g8zQS6ycazIL5pqZ0sht1
!
aaa
new-model
!
aaa
authentication login default local
aaa
authentication login sdm_vpn_xauth_ml_1 local
aaa
authorization exec default local
aaa
authorization network sdm_vpn_group_ml_1 local
!
aaa
session-id common
!
resource
policy
!
clock timezone
gmt 0
clock save interval 8
no ip dhcp use vrf connected
!
!
ip tcp synwait-time 10
ip cef
ip
name-server 8.8.8.8
!
ip tcp synwait-time 10
ip cef
ip
name-server 8.8.8.8
ip
name-server 192.168.0.15
ip
port-map user-pptp port tcp
5900 list 5
ip
port-map user-VNC port tcp 5900 list 3
ip
port-map user-VNC port tcp 5900 list 4
ip
port-map user-GRE port tcp 500 list 6
ip
inspect name SDM_LOW cuseeme
ip
inspect name SDM_LOW dns
ip
inspect name SDM_LOW ftp
ip
inspect name SDM_LOW h323
ip
inspect name SDM_LOW https
ip
inspect name SDM_LOW icmp
ip
inspect name SDM_LOW imap
ip
inspect name SDM_LOW netshow
ip
inspect name SDM_LOW rcmd
ip
inspect name SDM_LOW realaudio
ip
inspect name SDM_LOW rtsp
ip
inspect name SDM_LOW esmtp
ip
inspect name SDM_LOW sqlnet
ip
inspect name SDM_LOW streamworks
ip
inspect name SDM_LOW tftp
ip
inspect name SDM_LOW tcp
ip
inspect name SDM_LOW udp
ip
inspect name SDM_LOW vdolive
ip
inspect name SDM_LOW realaudio
ip
inspect name SDM_LOW rtsp
ip
inspect name SDM_LOW esmtp
ip
inspect name SDM_LOW sqlnet
ip
inspect name SDM_LOW streamworks
ip
inspect name SDM_LOW tftp
ip
inspect name SDM_LOW tcp
ip
inspect name SDM_LOW udp
ip
inspect name SDM_LOW vdolive
ip
inspect name SDM_LOW pop3
!
!
crypto pki trustpoint TP-self-signed-4146657400
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4146657400
revocation-check none
rsakeypair
TP-self-signed-4146657400
!
!
crypto pki
certificate chain TP-self-signed-4146657400
certificate self-signed 01
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
username me
privilege 15 password 7 secretxxx
!
!
!
crypto isakmp
policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp
key xxxx address 192.168.0.8 255.255.255.0
!
crypto isakmp
client configuration group me
key xxxxxxxx
pool SDM_POOL_1
max-users 5
authentication
pre-share
group 2
crypto isakmp
key xxxxx address 192.168.0.8 255.255.255.0
!
crypto isakmp
client configuration group me
key xxxxxxx
pool SDM_POOL_1
max-users 5
!
!
crypto ipsec
transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set ESP-3DES-SHA
reverse-route
!
!
crypto map SDM_CMAP_1 client
authentication list sdm_vpn_xauth_ml_1
crypto map SDM_CMAP_1 isakmp authorization list sdm_vpn_group_ml_1
crypto map SDM_CMAP_1 client
configuration address respond
crypto map SDM_CMAP_1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
!
!
!
interface
Ethernet0
description $ETH-LAN$$FW_INSIDE$
ip address 192.168.0.254
255.255.255.0
ip access-group 100 in
ip flow ingress
ip nat
inside
ip virtual-reassembly
ip route-cache flow
!
interface
Ethernet0
description $ETH-LAN$$FW_INSIDE$
ip address 192.168.0.254
255.255.255.0
ip access-group 100 in
ip flow ingress
ip nat
inside
ip virtual-reassembly
ip route-cache flow
hold-queue 100 out
!
interface
Ethernet2
no ip address
shutdown
hold-queue 100 out
!
interface
ATM0
no ip address
no atm ilmi-keepalive
dsl operating-mode auto
dsl enable-training-log
dsl lom
200
!
interface
ATM0.1 point-to-point
no snmp trap link-status
pvc 0/38
encapsulation aal5mux ppp dialer
dialer pool-member 1
!
!
interface
FastEthernet1
duplex auto
interface
ATM0.1 point-to-point
no snmp trap link-status
pvc 0/38
encapsulation aal5mux ppp dialer
dialer pool-member 1
!
!
interface
FastEthernet1
duplex auto
speed auto
!
interface
FastEthernet2
duplex auto
speed auto
!
interface
FastEthernet3
duplex auto
speed auto
!
interface
FastEthernet4
duplex auto
speed auto
!
interface
Dialer0
description $FW_OUTSIDE$
ip address negotiated
ip access-group 101 in
no ip redirects
ip flow ingress
ip nat
outside
ip inspect SDM_LOW in
ip inspect SDM_LOW out
ip virtual-reassembly
encapsulation ppp
ip route-cache flow
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname me@plusdsl.net
ppp chap password 7
0518120A37494B0F151C07155F
crypto map SDM_CMAP_1
!
ip
local pool SDM_POOL_1 192.168.0.150 192.168.0.160
ip
route 0.0.0.0 0.0.0.0 Dialer0
ip
http server
ip
http secure-server
ip dns server
ip nat pool LAN 192.168.0.1 192.168.0.99 netmask
255.255.255.0
ip nat source static esp 192.168.0.8
interface Dialer0
ip nat inside source static udp
192.168.0.8 1723 interface Dialer0 1723
ip nat inside source static udp
192.168.0.8 500 interface Dialer0 500
ip nat inside source static tcp
192.168.0.8 500 interface Dialer0 500
ip nat inside source static tcp
192.168.0.8 1723 interface Dialer0 1723
ip nat inside source route-map SDM_RMAP_1 interface Dialer0
overload
!
access-list 1
remark INSIDE_IF=Ethernet0
access-list 1
remark SDM_ACL Category=2
access-list 1
permit 192.168.0.0 0.0.0.255
access-list 2
remark SDM_ACL Category=2
access-list 2
permit 192.168.0.0 0.0.0.255
access-list 3
remark SDM_ACL Category=1
access-list 3
permit 192.168.0.15
access-list 4
remark SDM_ACL Category=1
access-list 4
permit 192.168.0.8
access-list 5
remark SDM_ACL Category=1
access-list 5
permit 192.168.0.8
access-list 6
remark SDM_ACL Category=1
access-list 6
permit 102.168.0.8
access-list
100 remark auto generated by SDM firewall configuration
access-list
100 remark SDM_ACL Category=1
access-list
100 deny ip
host 255.255.255.255 any
access-list
100 deny ip
127.0.0.0 0.255.255.255 any
access-list
100 permit ip any any
access-list
101 remark auto generated by SDM firewall configuration
access-list
101 remark SDM_ACL Category=1
access-list
101 permit tcp any any eq 1723
access-list
101 permit tcp any any eq 500
access-list
101 permit gre any any
access-list
101 permit udp any any eq 1723
access-list
101 remark Auto generated by SDM for NTP (123) 207.46.197.32
access-list
101 permit udp host 207.46.197.32 eq
ntp any eq ntp
access-list
101 remark Auto generated by SDM for NTP (123) 131.188.3.223
access-list
101 permit udp host 131.188.3.223 eq
ntp any eq ntp
access-list
101 permit ahp any any
access-list
101 permit esp any any
access-list
101 permit udp any any eq isakmp
access-list
101 permit udp any any eq non500-isakmp
access-list
101 deny ip
192.168.0.0 0.0.0.255 any
access-list
101 permit icmp any any
echo-reply
access-list
101 permit icmp any any
time-exceeded
access-list
101 permit icmp any any
unreachable
access-list
101 deny ip
10.0.0.0 0.255.255.255 any
access-list
101 deny ip
172.16.0.0 0.15.255.255 any
access-list
101 denyip
192.168.0.0 0.0.255.255 any
access-list
101 denyip
127.0.0.0 0.255.255.255 any
access-list
101 denyip
host 255.255.255.255 any
access-list
101 denyip
host 0.0.0.0 any
access-list
101 denyip
any any log
access-list
102 remark SDM_ACL Category=2
access-list
102 denyip
any host 192.168.0.150
access-list
101 denyip
10.0.0.0 0.255.255.255 any
access-list
101 denyip
172.16.0.0 0.15.255.255 any
access-list
101 denyip
192.168.0.0 0.0.255.255 any
access-list
101 denyip
127.0.0.0 0.255.255.255 any
access-list
101 denyip
host 255.255.255.255 any
access-list
101 denyip
host 0.0.0.0 any
access-list
101 denyip
any any log
access-list
102 remark SDM_ACL Category=2
access-list
102 denyip
any host 192.168.0.150
access-list
102 denyip
any host 192.168.0.151
access-list
102 denyip
any host 192.168.0.152
access-list
102 denyip
any host 192.168.0.153
access-list
102 denyip
any host 192.168.0.154
access-list
102 denyip
any host 192.168.0.155
access-list
102 denyip
any host 192.168.0.156
access-list
102 denyip
any host 192.168.0.157
access-list
102 denyip
any host 192.168.0.158
access-list
102 denyip
any host 192.168.0.159
access-list
102 denyip
any host 192.168.0.160
access-list
102 permit ip 192.168.0.0 0.0.0.255 any
dialer-list 1
protocol ip permit
route-map
SDM_RMAP_1 permit 1
match ip address 102
!
!
control-plane
!
banner motd
^C
Authorized access only
This system is the property of steve edwards.
Disconnect IMMEDIATELY as you are not an authorized user! ^C
!
line con 0
no modem enable
line aux 0
line vty
0 4
password 7 051B030A31
transport input ssh
!
scheduler
max-task-time 5000
scheduler
interval 500
sntp
server 131.188.3.223
sntp
server 207.46.197.32
end
The connection details after the stateful firewall is added via SDM:
Mar 23 07:30:01 firewall anacron[20519]: Anacron 2.3 started on 2011-03-23
Mar 23 07:30:01 firewall anacron[20519]: Normal exit (0 jobs run)
Mar 23 07:30:19 firewall pptpd[20575]: CTRL: Client 81.137.x.x control connection started
Mar 23 07:30:19 firewall pptpd[20575]: CTRL: Starting call (launching pppd, opening GRE)
Mar 23 07:30:19 firewall pppd[20576]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so loaded.
Mar 23 07:30:19 firewall kernel: [ 6244.469466] PPP generic driver version 2.4.2
Mar 23 07:30:19 firewall pppd[20576]: pppd 2.4.4 started by root, uid 0
Mar 23 07:30:19 firewall pppd[20576]: Using interface ppp0
Mar 23 07:30:19 firewall pppd[20576]: Connect: ppp0 <--> /dev/pts/2
Mar 23 07:30:19 firewall pptpd[20575]: GRE: Bad checksum from pppd.
Mar 23 07:30:21 firewall pptpd[20575]: CTRL: Ignored a SET LINK INFO packet with real ACCMs!
Mar 23 07:30:21 firewall kernel: [ 6246.917831] padlock: VIA PadLock Hash Engine not detected.
Mar 23 07:30:21 firewall modprobe: WARNING: Error inserting padlock_sha (/lib/modules/2.6.26-2-686/kernel/drivers/crypto/padlock-sha.ko): No such device
Mar 23 07:30:21 firewall kernel: [ 6246.923949] PPP MPPE Compression module registered
Mar 23 07:30:21 firewall pppd[20576]: MPPE 128-bit stateless compression enabled
Mar 23 07:30:24 firewall pppd[20576]: found interface eth0 for proxy arp
Mar 23 07:30:24 firewall pppd[20576]: local IP address 192.168.0.8
Mar 23 07:30:24 firewall pppd[20576]: remote IP address 192.168.0.200